Brute Force For Hash Mac
A brute-force attack on a MAC is a more difficult undertaking because it requires known message-MAC pairs. To attack a hash code, we can proceed in the following way. Given a fixed message x with n-bit hash code h = H(x), a brute-force method of finding a collision is to pick a. In this case, you can use John The Ripper to brute-force the disk images hash value via a wordlist and rules. First you need to install 'John the Ripper' (JtR). Best suited is the precompiled MacOS version. Linux versions available with apt for Debian lack the latest patches necessary for Sparseimage files. Get the password hash. The problem is the same - you do not want someone who obtained a message and the associated hash (MAC), be able to create new hashes (MACs) for other messages (as part of a brute-force attack). With one privatekey of 128-bit, I think we are good against brute force for two decades, with fair confidence. If there was billions privatekey and the adversary could obtain output for the same word for each of these privatekey, we would NOT be quite that safe with the 128-bit key size (the adversary has a remotely feasible task of finding. OnlineHashCrack is a powerful hash cracking and recovery online service for MD5 NTLM Wordpress Joomla SHA1 MySQL OSX WPA, PMKID, Office Docs, Archives, PDF, iTunes and more! How to configure a Bruteforce Attack Online Hash Crack.
- Brute Force For Hash Machine
- Brute Force For Hash Machine Learning
- Brute Force For Hash Macaroni
- Brute Force For Hash Mac Dre
- Brute Force For Hash Mac And Cheese
In cryptography, a collision attack on a cryptographic hash tries to find two inputs producing the same hash value, i.e. a hash collision. This is in contrast to a preimage attack where a specific target hash value is specified.
There are roughly two types of collision attacks:
- Collision attack
- Find two different messages m1 and m2 such that hash(m1) = hash(m2).

More generally:
- Chosen-prefix collision attack
- Given two different prefixes p1 and p2, find two appendages m1 and m2 such that hash(p1 ∥ m1) = hash(p2 ∥ m2), where ∥ denotes the concatenation operation.
Classical collision attack[edit]
Mathematically stated, a collision attack finds two different messages m1 and m2, such that hash(m1) = hash(m2). In a classical collision attack, the attacker has no control over the content of either message, but they are arbitrarily chosen by the algorithm.
Much like symmetric-key ciphers are vulnerable to brute force attacks, every cryptographic hash function is inherently vulnerable to collisions using a birthday attack. Due to the birthday problem, these attacks are much faster than a brute force would be. A hash of n bits can be broken in 2n/2 time (evaluations of the hash function).
More efficient attacks are possible by employing cryptanalysis to specific hash functions. When a collision attack is discovered and is found to be faster than a birthday attack, a hash function is often denounced as 'broken'. The NIST hash function competition was largely induced by published collision attacks against two very commonly used hash functions, MD5[1] and SHA-1. The collision attacks against MD5 have improved so much that, as of 2007, it takes just a few seconds on a regular computer.[2] Hash collisions created this way are usually constant length and largely unstructured, so cannot directly be applied to attack widespread document formats or protocols.
However, workarounds are possible by abusing dynamic constructs present in many formats. In this way, two documents would be created which are as similar as possible in order to have the same hash value. One document would be shown to an authority to be signed, and then the signature could be copied to the other file. Such a malicious document would contain two different messages in the same document, but conditionally display one or the other through subtle changes to the file:
- Some document formats like PostScript, or macros in Microsoft Word, have conditional constructs.[3][4] (if-then-else) that allow testing whether a location in the file has one value or another in order to control what is displayed.
- TIFF files can contain cropped images, with a different part of an image being displayed without affecting the hash value.[4]
- PDF files are vulnerable to collision attacks by using color value (such that text of one message is displayed with a white color that blends into the background, and text of the other message is displayed with a dark color) which can then be altered to change the signed document's content.[4]

Chosen-prefix collision attack[edit]
An extension of the collision attack is the chosen-prefix collision attack, which is specific to Merkle–Damgård hash functions. In this case, the attacker can choose two arbitrarily different documents, and then append different calculated values that result in the whole documents having an equal hash value. This attack is much more powerful than a classical collision attack.
Mathematically stated, given two different prefixes p1, p2, the attack finds two appendages m1 and m2 such that hash(p1 ∥ m1) = hash(p2 ∥ m2) (where ∥ is the concatenation operation).
In 2007, a chosen-prefix collision attack was found against MD5, requiring roughly 250 evaluations of the MD5 function. The paper also demonstrates two X.509 certificates for different domain names, with colliding hash values. This means that a certificate authority could be asked to sign a certificate for one domain, and then that certificate (specially its signature) could be used to create a new rogue certificate to impersonate another domain.[5]
A real-world collision attack was published in December 2008 when a group of security researchers published a forged X.509 signing certificate that could be used to impersonate a certificate authority, taking advantage of a prefix collision attack against the MD5 hash function. This meant that an attacker could impersonate any SSL-secured website as a man-in-the-middle, thereby subverting the certificate validation built in every web browser to protect electronic commerce. The rogue certificate may not be revokable by real authorities, and could also have an arbitrary forged expiry time. Even though MD5 was known to be very weak in 2004,[1] certificate authorities were still willing to sign MD5-verified certificates in December 2008,[6] and at least one Microsoft code-signing certificate was still using MD5 in May 2012.
The Flame malware successfully used a new variation of a chosen-prefix collision attack to spoof code signing of its components by a Microsoft root certificate that still used the compromised MD5 algorithm.[7][8]
In 2019, researchers found a chosen-prefix collision attack against SHA-1 with computing complexity between 266.9 and 269.4 and cost less than 100,000 US dollars. [9][10] In 2020, researchers reduced the complexity of chosen-prefix collision attack against SHA-1 to 263.4. [11]
Attack scenarios[edit]
Many applications of cryptographic hash functions do not rely on collision resistance, thus collision attacks do not affect their security. For example, HMACs are not vulnerable.[12] For the attack to be useful, the attacker must be in control of the input to the hash function.
Digital signatures[edit]
Because digital signature algorithms cannot sign a large amount of data efficiently, most implementations use a hash function to reduce ('compress') the amount of data that needs to be signed down to a constant size. Digital signature schemes are often vulnerable to hash collisions, unless using techniques like randomized hashing.[13]
The usual attack scenario goes like this:
- Mallory creates two different documents A and B that have an identical hash value, i.e., a collision. Mallory seeks to deceive Bob into accepting document B, ostensibly from Alice.
- Mallory sends document A to Alice, who agrees to what the document says, signs its hash, and sends the signature to Mallory.
- Mallory attaches the signature from document A to document B.
- Mallory then sends the signature and document B to Bob, claiming that Alice signed B. Because the digital signature matches document B's hash, Bob's software is unable to detect the substitution.
In 2008, researchers used a chosen-prefix collision attack against MD5 using this scenario, to produce a rogue certificate authority certificate. They created two versions of a TLSpublic key certificate, one of which appeared legitimate and was submitted for signing by the RapidSSL certificate authority. The second version, which had the same MD5 hash, contained flags which signal web browsers to accept it as a legitimate authority for issuing arbitrary other certificates.[14]
Usage in DoS attacks[edit]
In 2003, a denial of service (DoS) attack was described that used hash collisions to exploit the worst-case runtime of hash table lookups.[15] This issue affected most major programming languages, as they used weaker hash functions.
References[edit]
- ^ abXiaoyun Wang, Dengguo Feng, Xuejia Lai, Hongbo Yu: Collisions for Hash Functions MD4, MD5, HAVAL-128 and RIPEMD, Cryptology ePrint Archive Report 2004/199, 16 Aug 2004, revised 17 Aug 2004. Retrieved July 27, 2008.
- ^M.M.J. Stevens (June 2007). 'On Collisions for MD5'(PDF).
[...] we are able to find collisions for MD5 in about 224.1 compressions for recommended IHVs which takes approx. 6 seconds on a 2.6GHz Pentium 4.
Cite journal requires|journal=(help) - ^Magnus Daum; Stefan Lucks. 'Hash Collisions (The Poisoned Message Attack)'. Eurocrypt 2005 rump session. Archived from the original on 2010-03-27.
- ^ abcMax Gebhardt; Georg Illies; Werner Schindler. 'A Note on the Practical Value of Single Hash Collisions for Special File Formats'(PDF).Cite journal requires
|journal=(help) - ^Marc Stevens; Arjen Lenstra; Benne de Weger (2007-11-30). 'Chosen-prefix Collisions for MD5 and Colliding X.509 Certificates for Different Identities'.Cite journal requires
|journal=(help) - ^Alexander Sotirov; et al. (2008-12-30). 'Creating a rogue CA certificate'. Archived from the original on 2012-04-18. Retrieved 2009-10-07.
- ^'Microsoft releases Security Advisory 2718704'. Microsoft. 3 June 2012. Archived from the original on 7 June 2012. Retrieved 4 June 2012.
- ^Marc Stevens (7 June 2012). 'CWI Cryptanalist Discovers New Cryptographic Attack Variant in Flame Spy Malware'. Centrum Wiskunde & Informatica. Retrieved 9 June 2012.
- ^Catalin Cimpanu (2019-05-13). 'SHA-1 collision attacks are now actually practical and a looming danger'. ZDNet.
- ^Ga¨etan Leurent1 and Thomas Peyrin (2019-05-06). 'From Collisions to Chosen-Prefix Collisions Application to Full SHA-1'(PDF).
- ^Gaëtan Leurent and Thomas Peyrin (2020-01-05). 'SHA-1 is a Shambles - First Chosen-Prefix Collision on SHA-1 and Application to the PGP Web of Trust'(PDF).
- ^'Hash Collision Q&A'. Cryptography Research Inc. 2005-02-15. Archived from the original on 2008-07-17.
Because of the way hash functions are used in the HMAC construction, the techniques used in these recent attacks do not apply
- ^Shai Halevi and Hugo Krawczyk, Randomized Hashing and Digital Signatures
- ^Alexander Sotirov; Marc Stevens; Jacob Appelbaum; Arjen Lenstra; David Molnar; Dag Arne Osvik; Benne de Weger (30 December 2008). MD5 considered harmful today. Chaos Communication Congress 2008.
- ^'Hash DoS Attack'. Crossmatch, part of HID Global. Retrieved 2019-08-17.
External links[edit]
- Fast MD5 and MD4 Collision Generators - Bishop Fox (formerly Stach & Liu). Create MD4 and MD5 hash collisions using groundbreaking new code that improves upon the techniques originally developed by Xiaoyun Wang. Using a 1.6 GHz Pentium 4, MD5 collisions can be generated in an average of 45 minutes, and MD4 collisions can be generated in an average of 5 seconds. Originally released on 22Jun2006.
In this tutorial we will show you how to perform a mask attack in hashcat.
We will specify masks containing specific ranges using the command line and with hashcat mask files.
To demonstrate, we will perform a mask attack on a MD5 hash of the password “Mask101”.
This guide is demonstrated using the Kali Linux operating system by Offensive Security. Some commands may differ on other systems but the process is the same.
What Is a Mask Attack?
Mask attacks are similar to brute-force attacks given they try all combinations from a set of characters. With brute-force attacks, all possible characters that exist are tried. Mask attacks are more specific as the set of characters you try is reduced based on information you know.
For example, if you know the last character in a password is a number, you can configure your mask to only try numbers at the end. Using traditional brute-force attacks, you would still be forced to try characters that are not numbers.
This matters because the total combination of characters to exhaust with a masking attack is smaller.
For example, if we take the following password:
It has a length of 7 characters and for each one, it could be upper-case (26 potential characters), lower-case (26 potential characters), a symbol (33 potential characters) or a number (10 potential characters), we’d have to try a total number of 95^7 (69,833,728,698,375) combinations.
Now suppose we know the last three characters are numbers. This would drastically reduce the potential keyspace as no passwords with any letter or symbol in the last three spaces would need to be tried.
Of course you need to make sure your information on the password is correct, otherwise your mask may not generate the password. Using masking you can also create masks to exploit password habits. For example, a common habit is for passwords to start with a capital if at least one is required.
Another example where masking can be applied is that if default passwords schemes use a known set of characters. A lot of home router's have default password generation algorithms and information about their keyspace can be found online.
Creating an MD5 Hashed Password To Use
To start, we need to generate the hash. On my system running Kali Linux, I can run the following command to generate a file containing the hashed word:
This command is explained in a previous blog post but to summarise it creates an MD5 hash of whatever text is echoed and stores it in a file called hash.
If that doesn’t work on your system you can run this command to store the hashed password in a file:
Understanding the hashcat parameters
So now that we have the hash we want to perform our mask attack on, we will now define our mask.
To speed up the process of the cracking, we are going to base this attack on us knowing the last three characters are numbers and the first one is also a capital letter. Knowing this, as already explained will reduce the number of combinations needed to try even more.
From the output of “hashcat –help” we'll use the following information to perform our mask attack:
Based on the above the start of our command looks like the following:
So far we are specifying our hash as MD5 (-m 0) and our attack mode as a brute-force (-a 3).
Note that although this method isn’t regarded as a proper brute-force attack, it has replaced the brute-forcing function in hashcat. This is because it’s possible to perform a traditional brute-force attack if the mask specifies every possible character to try.
Below are the mask commands from “hashcat --help”
We can see that the built-in charsets can be used to specify a useful range of characters. However, in our case, we need to be more specific. To do this, we will create a custom charset which makes our next portion of the command like so:
Here we are creating three different character sets. The “?” followed by either “l”, “u”, “d’ characters are used to access the built-in charsets available (see “hashcat --help” output above for more details).
This means our custom charsets -1,-2 and -3 are equal to:
| Charset | Contains the charcters |
| -1 | ABCDEFGHIJKLMNOPQRSTUVWXYZ |
| -2 | abcdefghijklmnopqrstuvwxyz ABCDEFGHIJKLMNOPQRSTUVWXYZ 0123456789 |
| -3 | 0123456789 |
Now that they are defined, we need to specify for every character which charset to use. For example, we know in our password that the first character is uppercase. So for the first character we want to use the character set “-1”.
To specify the character sets for all eight characters of the password in command form, we would do the following:
Putting this all together, the full command that will run our masking attack looks like:
The word “hash” refers to the file we created earlier containing the hashed password.
Running the Mask Attack
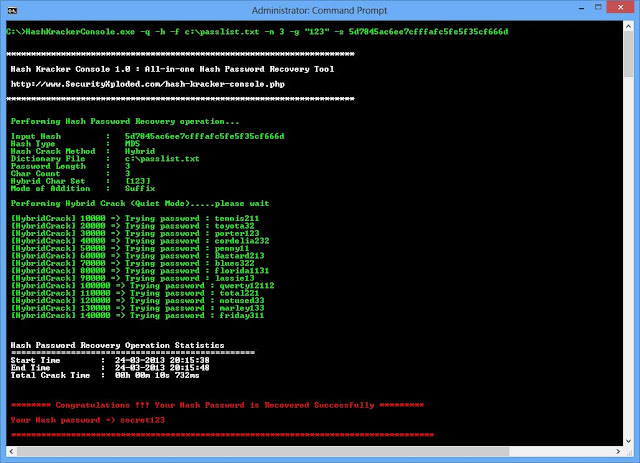
After running the command, the attack will start and you should get output similar to the following:
From the above output, we can see the password hash was recovered.
In this attack another assumption we made is that the user has not used any symbols in their password, making the attack much faster. The attack is also based on the assumption the password is seven characters long.
The --increment Argument
A useful option to know about is “--increment”. If you take the mask “?l?l?l?l?l?l?l” it will only try passwords of that length. To cycle through all the possible combinations from one to seven, the “--increment argument” can be used.
This essentially means adding “--increment” will go through all combinations like so:
In the case of our attack, this would make the mask we tried look like the following:
Hashcat Mask Files
Consider the following scenario for creating a password masking attack:
- Length between five and eight characters
- Always starts with a capital letter
- Always ends with a number
- The characters in the middle are either lower or upper case
With what we've learned, can we express the above conditions to hashcat to exhaust the keyspace above?
The answer is No. For instance we can't tell hashcat that character seven in a password of length seven is a number, yet character seven in an eight character password is an alpha.
This is where mask files come in. With Mask files you can specify multiple masking options, point hashcat to the file and all the attacks will be run.
Brute Force For Hash Machine
For a single entry in a mask file, the following structure is used:
It's important to highlight that the charset parameters are optional. So it's possible to create entries in the following format:
To meet the previous scenario, we can create a mask file containing the following:
Mask files have the file extension of '.hcmask' and can be used from the command line like below:
Brute Force For Hash Machine Learning
Summary
In this guide we have covered how to perform a mask attack using hashcat. A command line mask attack has been demonstrated and a mask file attack. The advantages of mask files has also been highlighted and the use of the '--increment' option has been explained.
Brute Force For Hash Macaroni
Mask Attack Challenge
Now that you've been through a step-by-step demonstration and seen an example of a mask file, it's time to put your new skills to the test!
With the MD5 hash below:
And using the following information about the password:
- Between five and nine characters long
- Contains a symbol
- Contains a capital letter
- Doesn't contain any numbers
Your challenge is to create an appropriate mask file and break the hash.
Based on the information above, these are the types of questions you should consider:
Brute Force For Hash Mac Dre
- Where could the symbol likely be located?
- Where could the capital letter likely be located?
Brute Force For Hash Mac And Cheese
If you were making a password, where would you most likely put them?
Also consider what the other characters could be based on the information supplied.
It's worth noting that this one will take longer to crack than the example, however it shouldn't take a massive amount of time. Each hint combined forms part of the bigger picture for this challenge. If you take all of them into account, you will be able to crack the hash.